New Open-Source Malware Puts Bitcoin and Crypto Wallets at Risk

A new danger has surfaced that targets Bitcoin and crypto wallets. The MacOS Stealer Trojan, once a premium piece of malware sold for 1 BTC, has now been unleashed into the wild as open-source software. This shift dramatically increases its accessibility to cybercriminals, intensifying the threat level for MacOS users who hold digital currencies.
This malware is particularly insidious. It doesn't just lurk; it actively preys on users through deceptive means. Often masquerading as legitimate job offers, verification bots, or seemingly innocuous software downloads, it tricks users into granting it access to their systems. Once inside, the Trojan methodically siphons off sensitive data, including wallet credentials and private keys, which are the keys to one's digital treasure chest. The consequences of such an intrusion can be catastrophic, leading to the loss of assets that might never be recovered.
The Escalating Threat
The decision to make the MacOS Stealer Trojan open-source has transformed it from a tool used by a select few into a weapon in the hands of many. Security researchers at Slowmist have highlighted how this development allows for a proliferation of similar, if not more advanced, theft mechanisms. Hackers can now modify, improve, and distribute this malware at a pace that outstrips many security measures currently in place. This shift not only makes attacks more potent and harder to detect but also signals a new era where the tools of cybercrime are as freely available as the software they mimic.
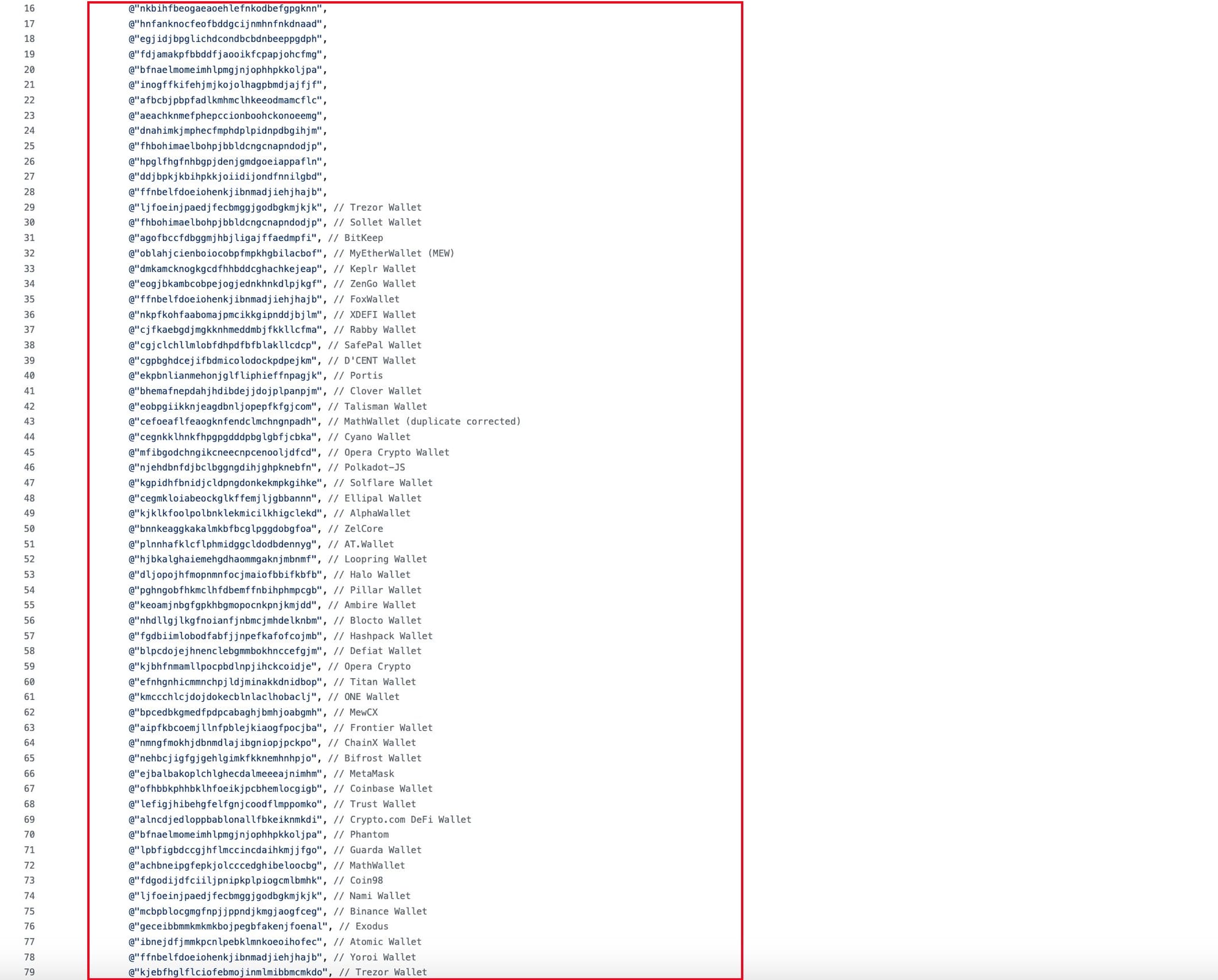
The malware targets specific crypto wallets, and according to the alert, wallets like Trezor, Bitkeep, Metamask, Coinbase Wallet, Trust Wallet, Crypto.com Wallet, Binance Wallet, Exodus, and many others are being targeted by this stealer trojan.
The implications for cryptocurrency users are urgent. Each new variant or derivative of this malware could mean another layer of complexity in defending one's digital assets.
The safest storage for cryptocurrencies remains hardware wallets, which offer a physical barrier against attackers, although even with a hardware wallet they are also susceptible to this attack if your computer is compromised. Installing software should be approached with a detective's eye, ensuring every piece of code is from a trusted source. Before any new software becomes part of your system, a thorough security scan should be routine, acting as a gatekeeper to your digital world.

